Microsoft Defender
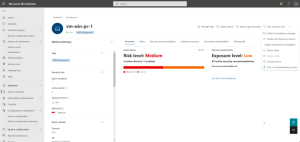
What is Microsoft Defender for Business?
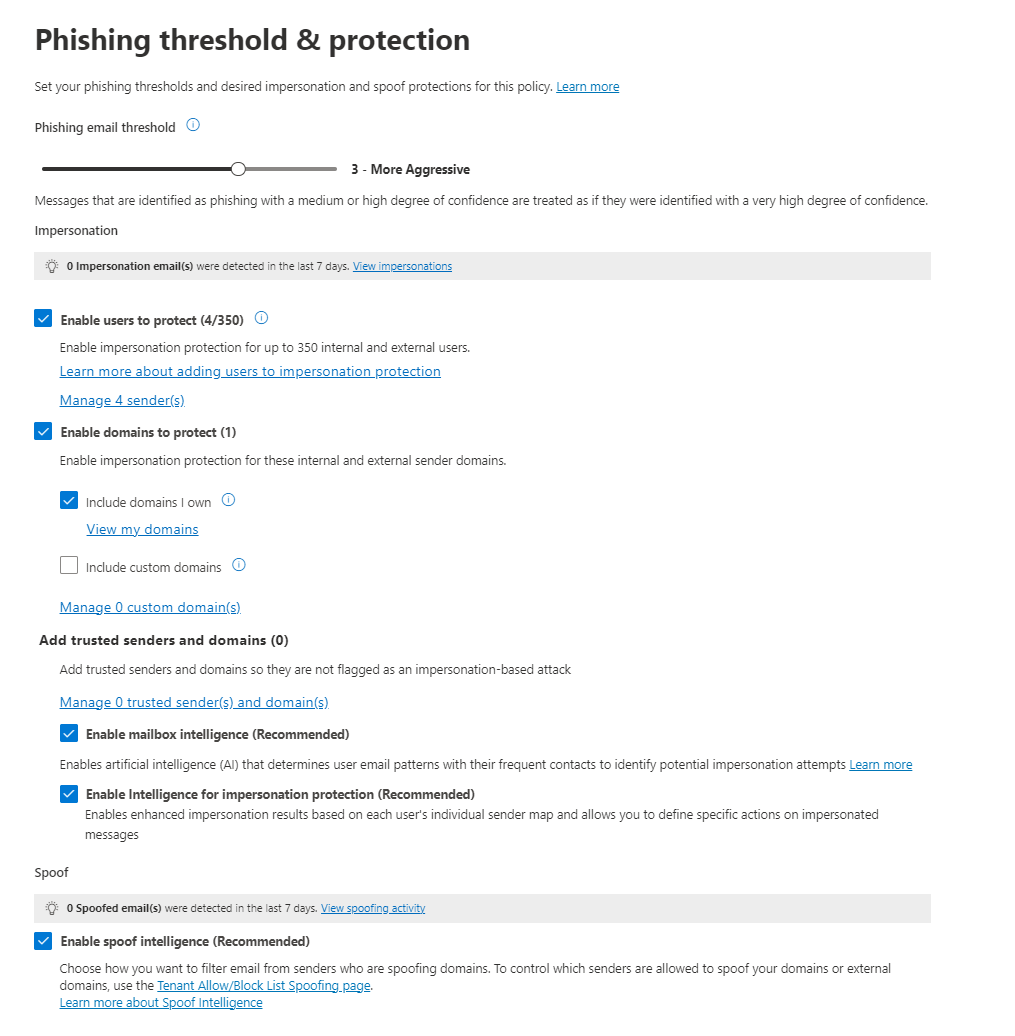
Microsoft Defender is a comprehensive security solution built into Windows, designed to protect your devices from a wide range of cyber threats. It includes robust antivirus protection, real-time threat detection, and a firewall to safeguard your system against malware, viruses, and ransomware. Defender’s features extend beyond basic antivirus, incorporating advanced tools like cloud-based protection, which utilizes Microsoft’s vast threat intelligence network to identify and mitigate emerging threats quickly.
It also offers performance monitoring and privacy controls to ensure safe browsing and system health. Regular updates and seamless integration with Windows make Microsoft Defender a convenient choice for maintaining security without additional software. Its integration with Microsoft 365 provides enhanced security features for enterprise environments, making it a versatile solution for both personal and professional use.
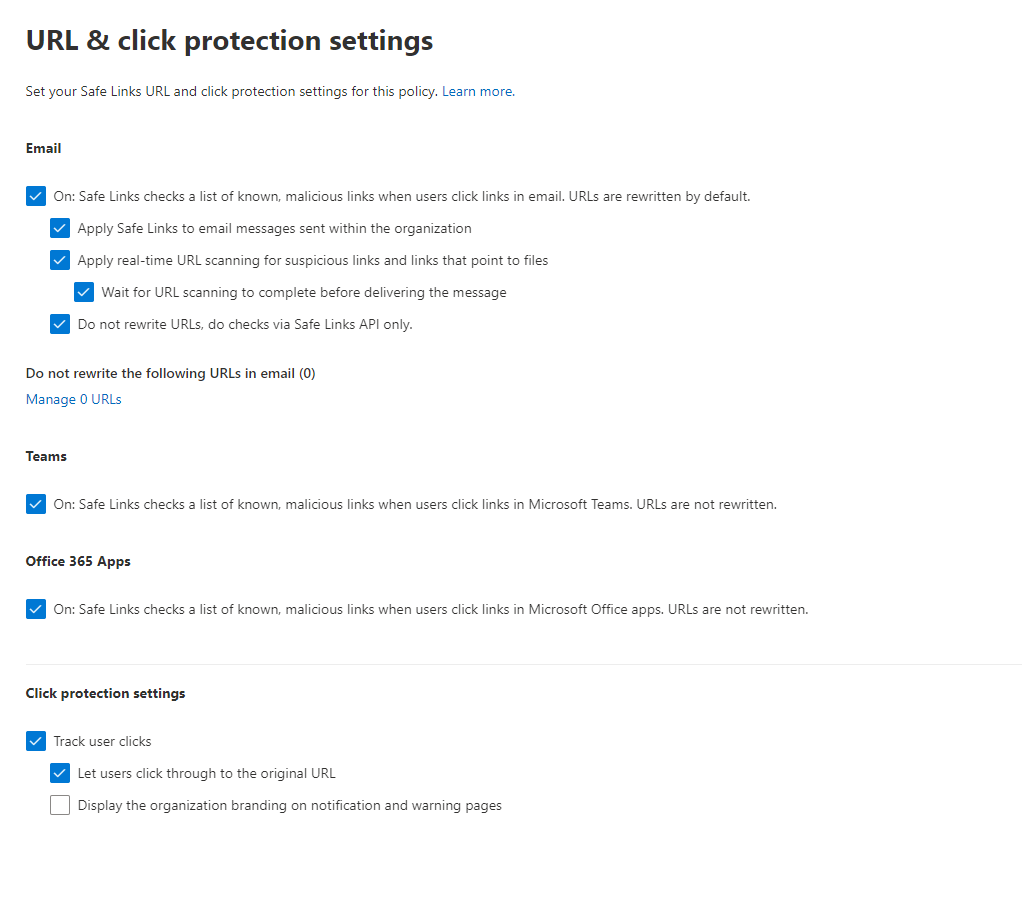
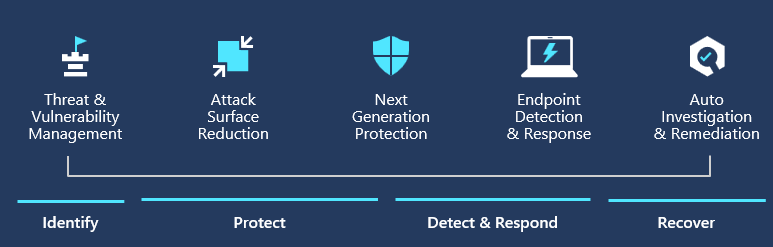
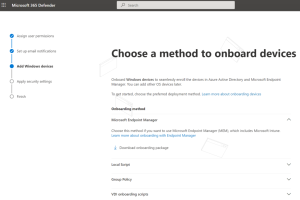
- Endpoint Protection
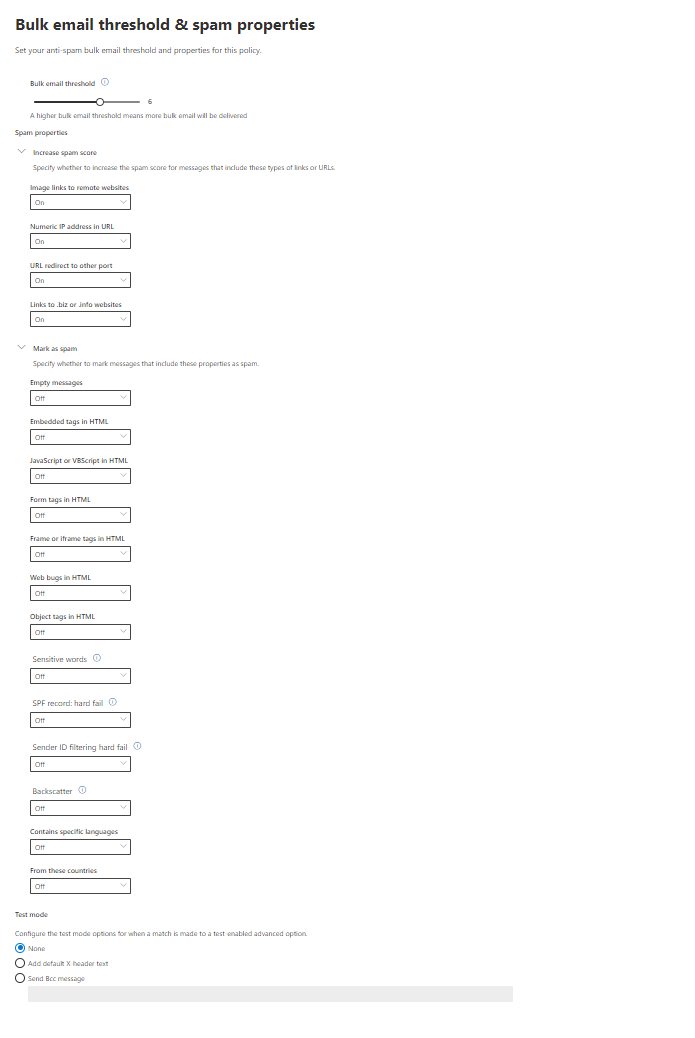
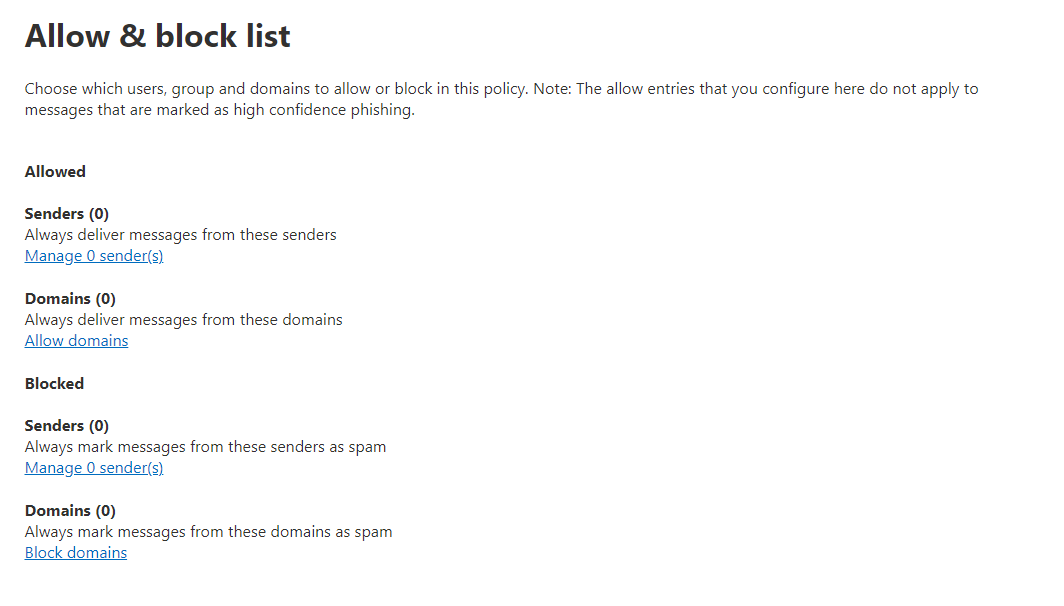
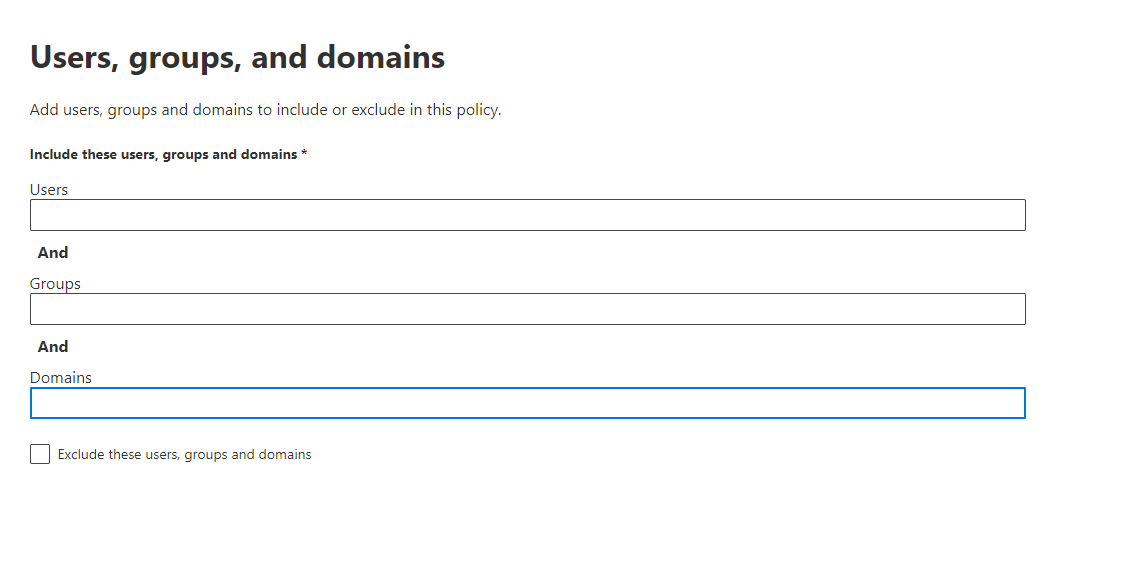
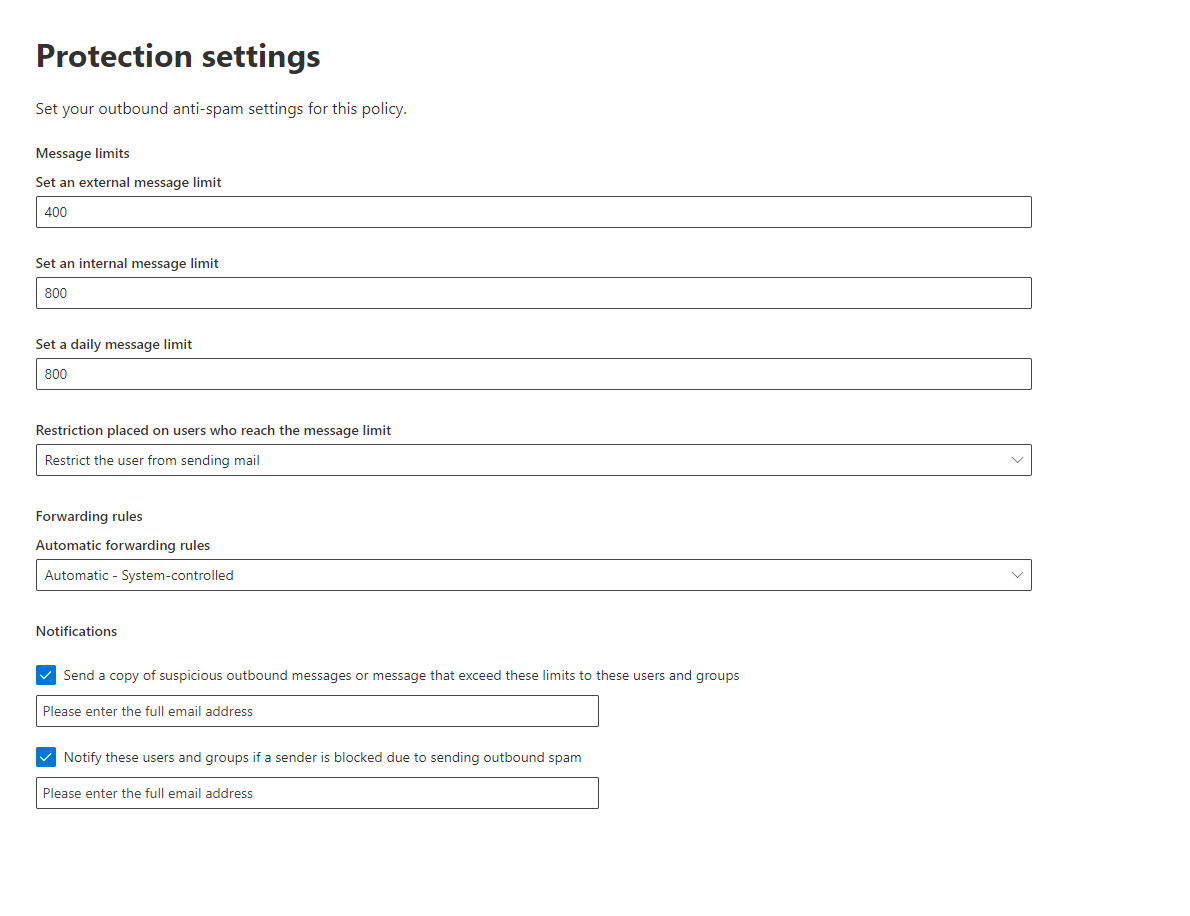
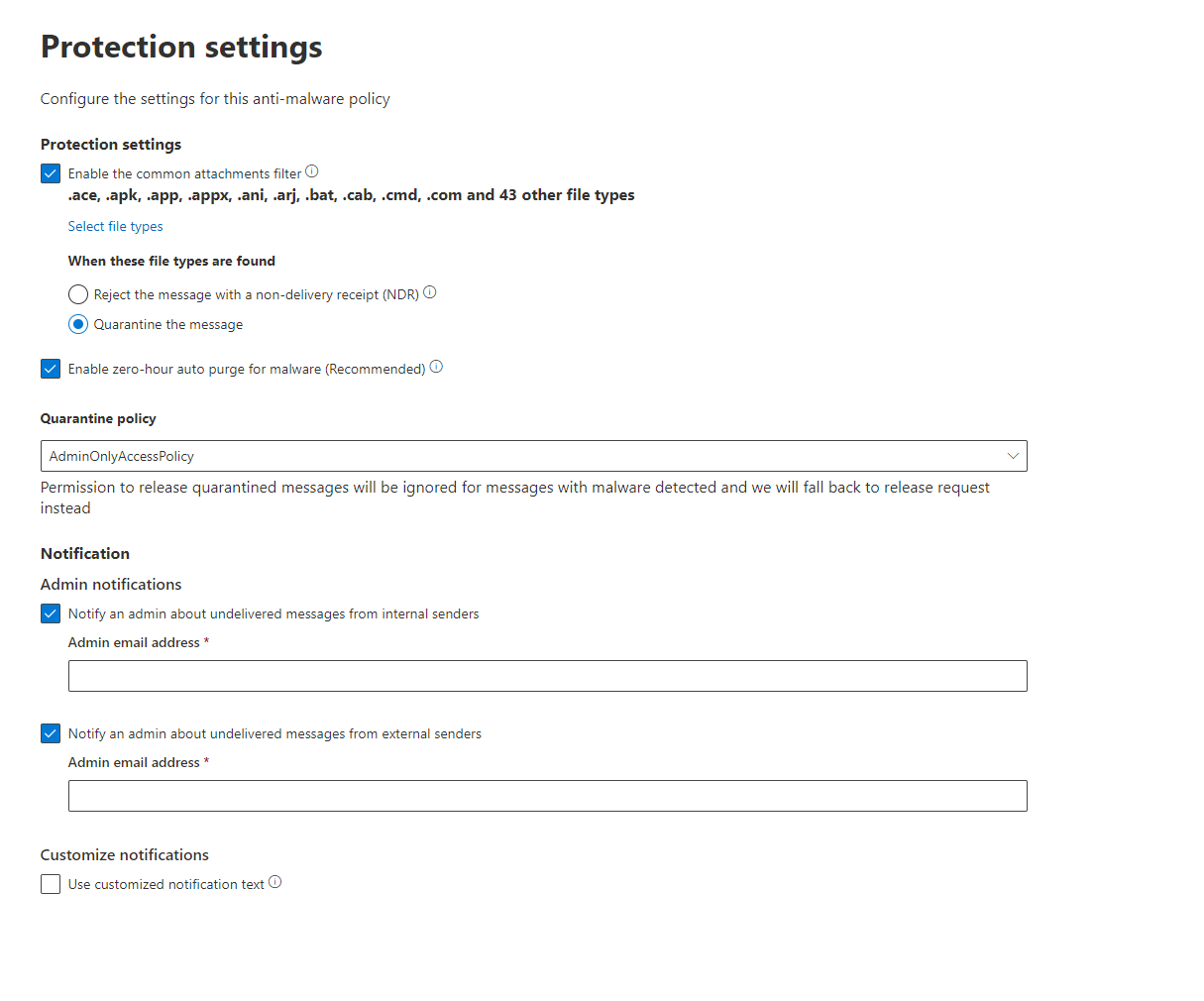
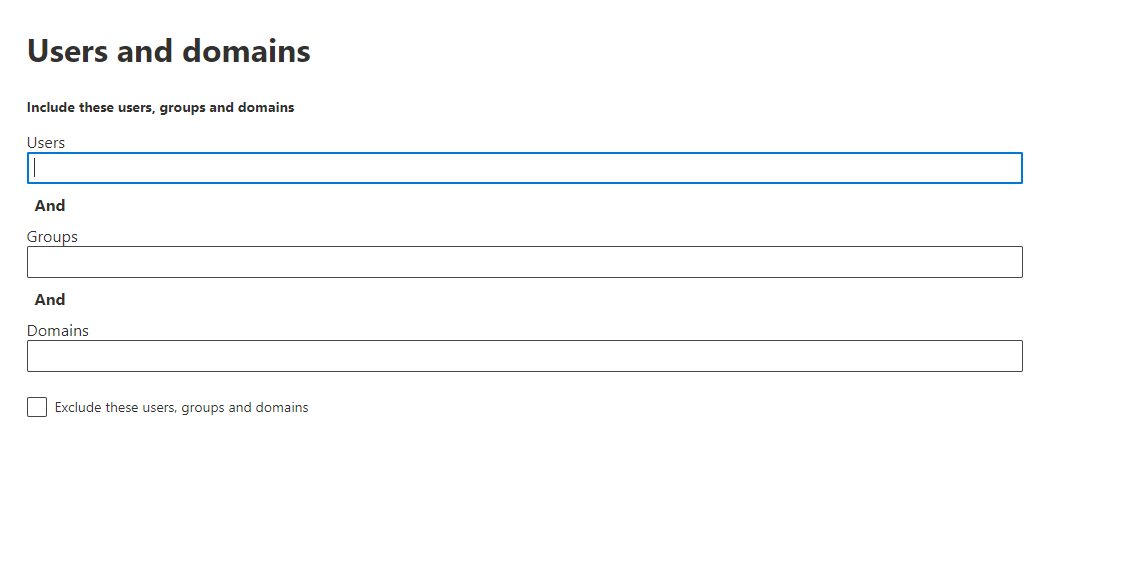
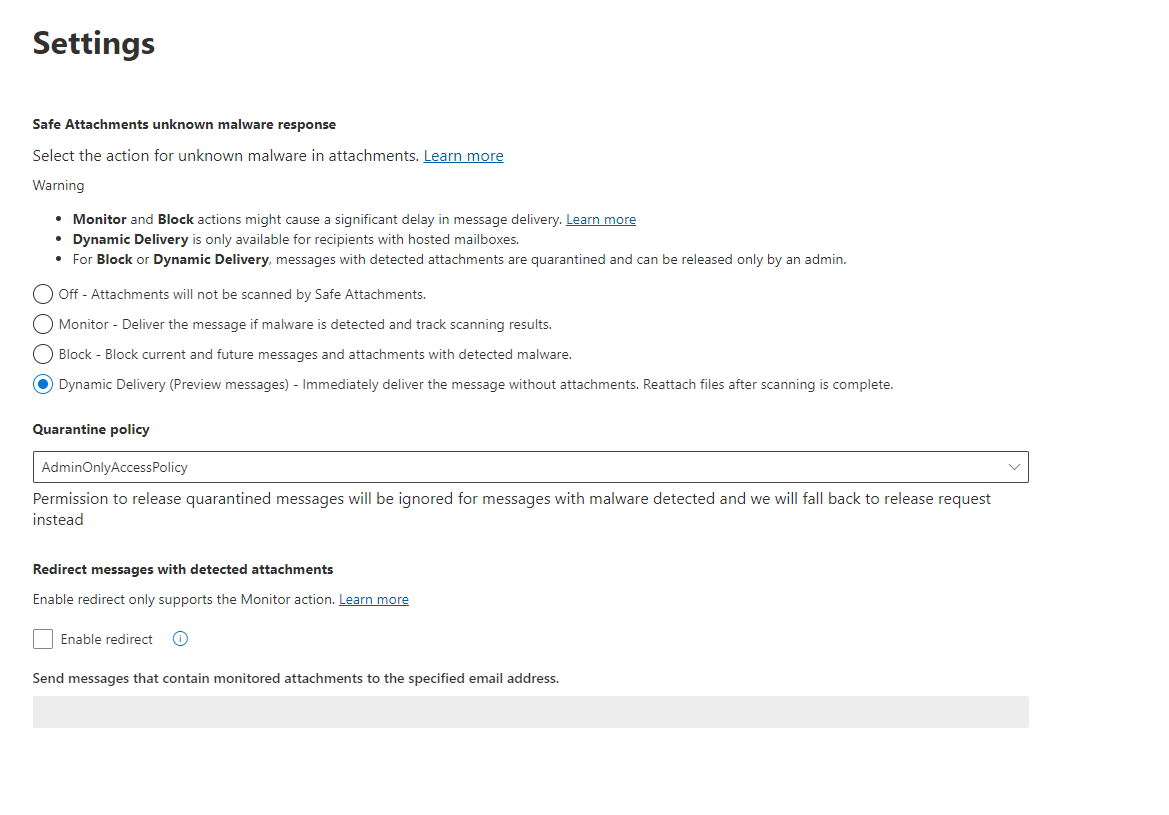
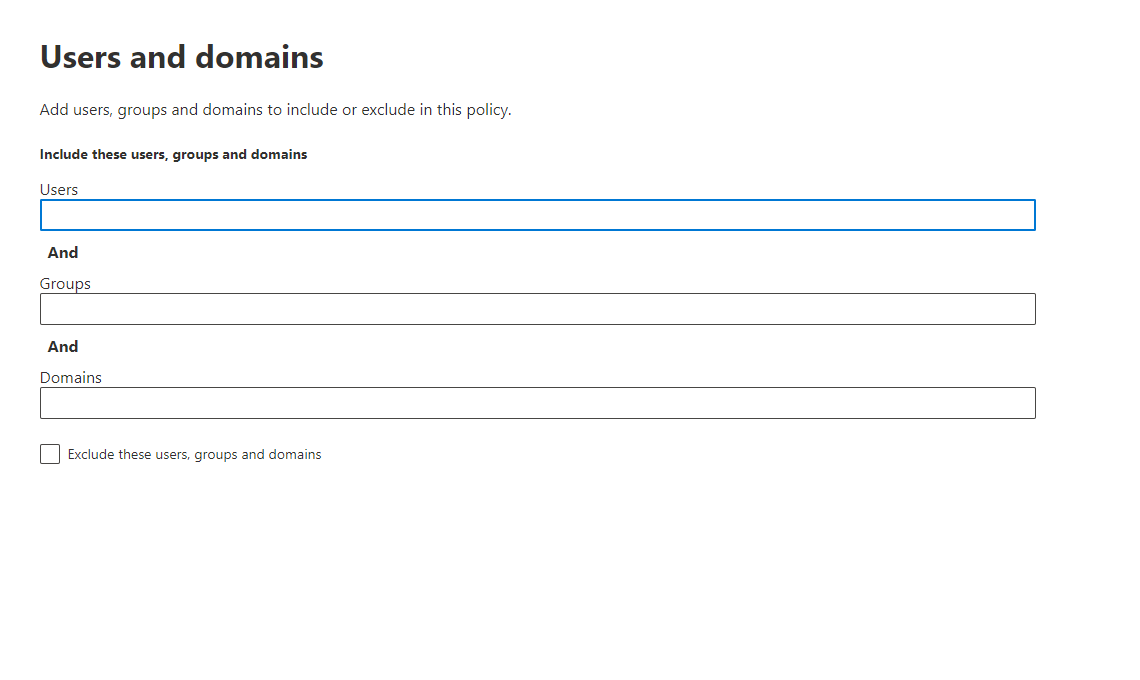
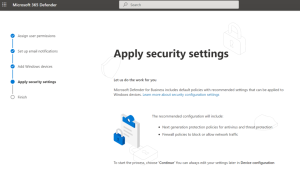
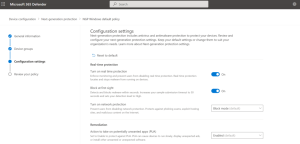
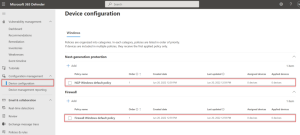
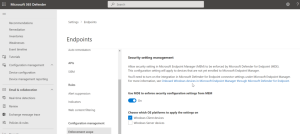
Defender for Business offers real-time protection against viruses, malware, ransomware, and other threats across all endpoints within the organization. It utilizes machine learning models and behavioral analytics to detect and block malicious activities.
- Advanced Threat Protection
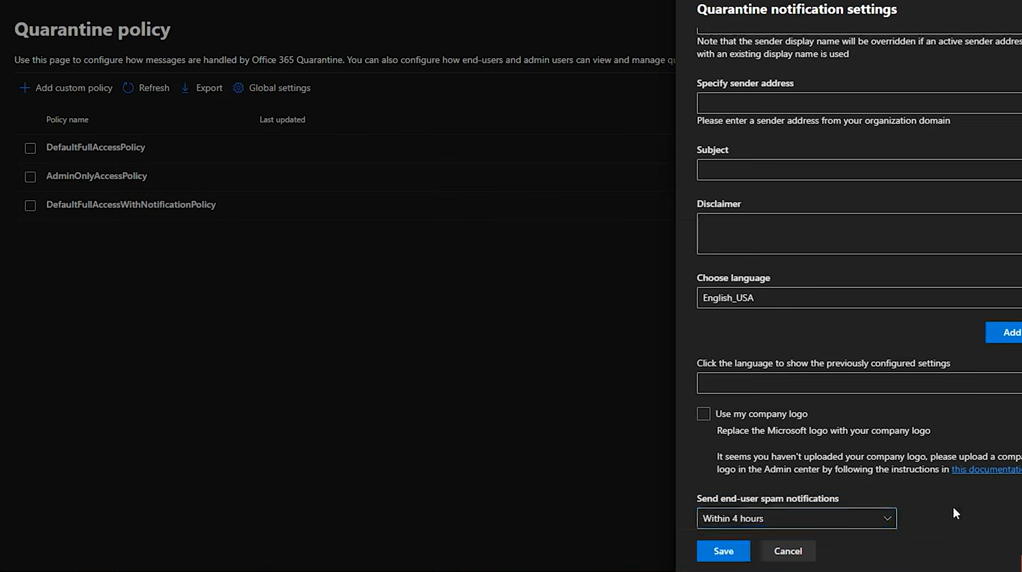
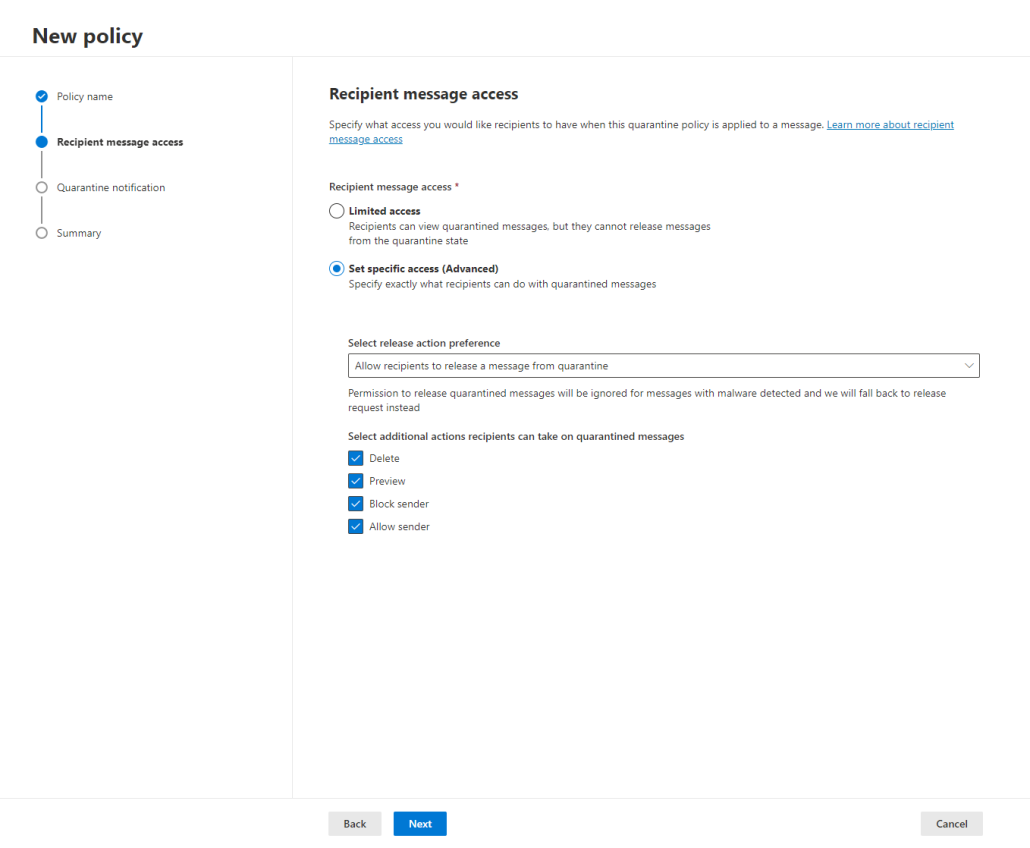
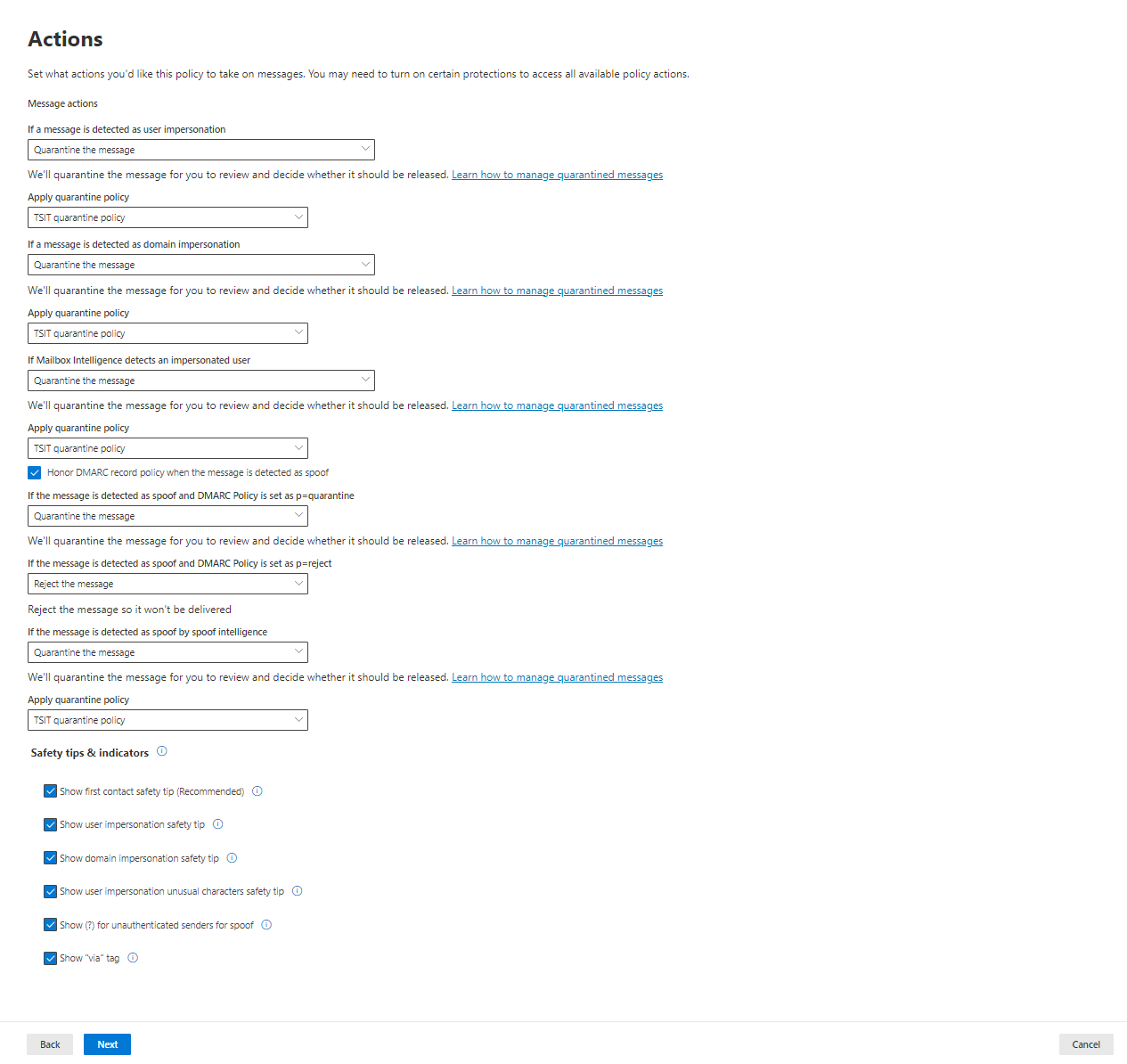
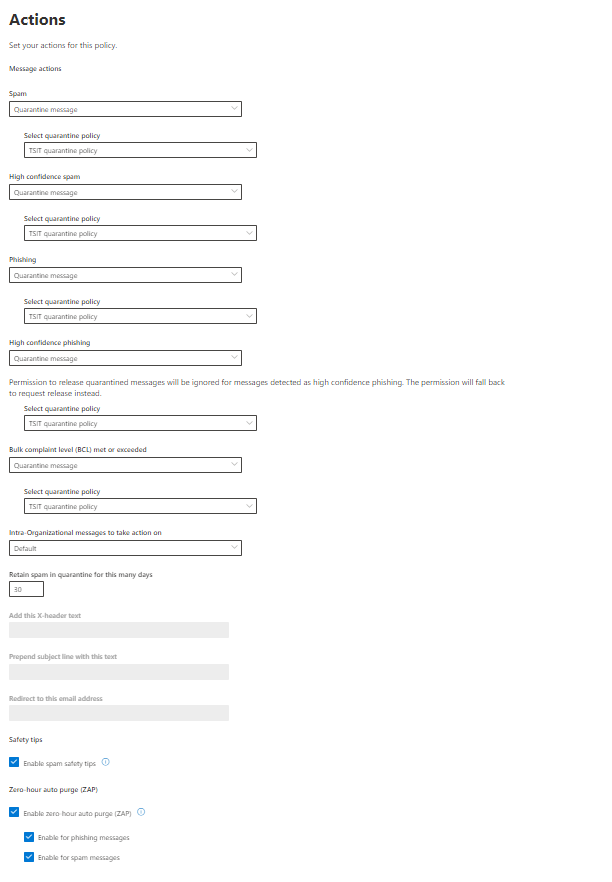
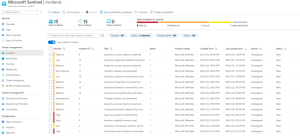
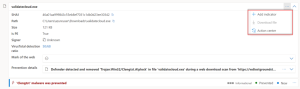
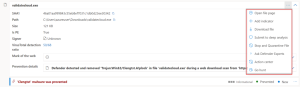
The solution includes advanced threat protection capabilities such as endpoint detection and response (EDR), which allows businesses to detect, investigate, and respond to advanced threats and breaches.
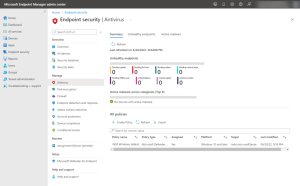
- Endpoint Detection and Response (EDR)
Defender for Business provides EDR capabilities to enable organizations to investigate and respond to advanced threats and security incidents across their endpoints. It allows security teams to analyze endpoint activities, conduct forensic investigations, and take appropriate response actions.