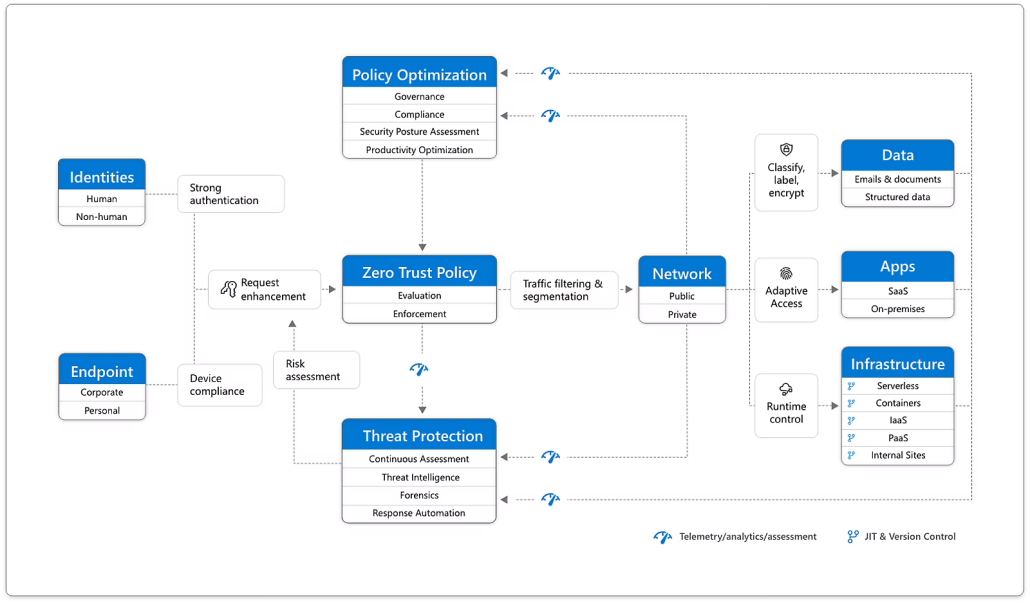
Zero Trust Framework
By employing solutions rooted in a Zero Trust Framework, Microsoft consistently adopts a “never trust, always verify” stance towards security.
Rather than presuming the safety of everything within a corporate firewall, the Zero Trust model operates on the assumption of breaches, verifies explicitly, and employs the principle of least privileged access.